

Stop account takeovers and defend identities to stop lateral movement
See how our customers discover and remediate their identity vulnerabilities before their adversaries do.
More than 80% of today's cyber attacks involve compromised user accounts and identities.
Once attackers have control of legitimate accounts, without effective identity security, they can navigate and move around the environment at will. This is how a minor security incident turns into a major business impacting breach.
Remediate vulnerable identities, close off attack paths and stop attacks in real time.
Accelerate active threat detection and response to reduce dwell time.
Detect and resolve compromised accounts in minutes, not days.
Proofpoint Identity Protection remains undefeated in more than 160 red-team exercises (and counting).
Accelerate active threat detection and response to reduce dwell time
Stop account takeovers and protect privileged identities with integrated security controls that span the attack chain. Discover identity vulnerabilities before an attack. Automatically prioritize and remediate the riskiest vulnerabilities and detect active threats in real-time across the broadest range of IT resources, both cloud and on-premises.
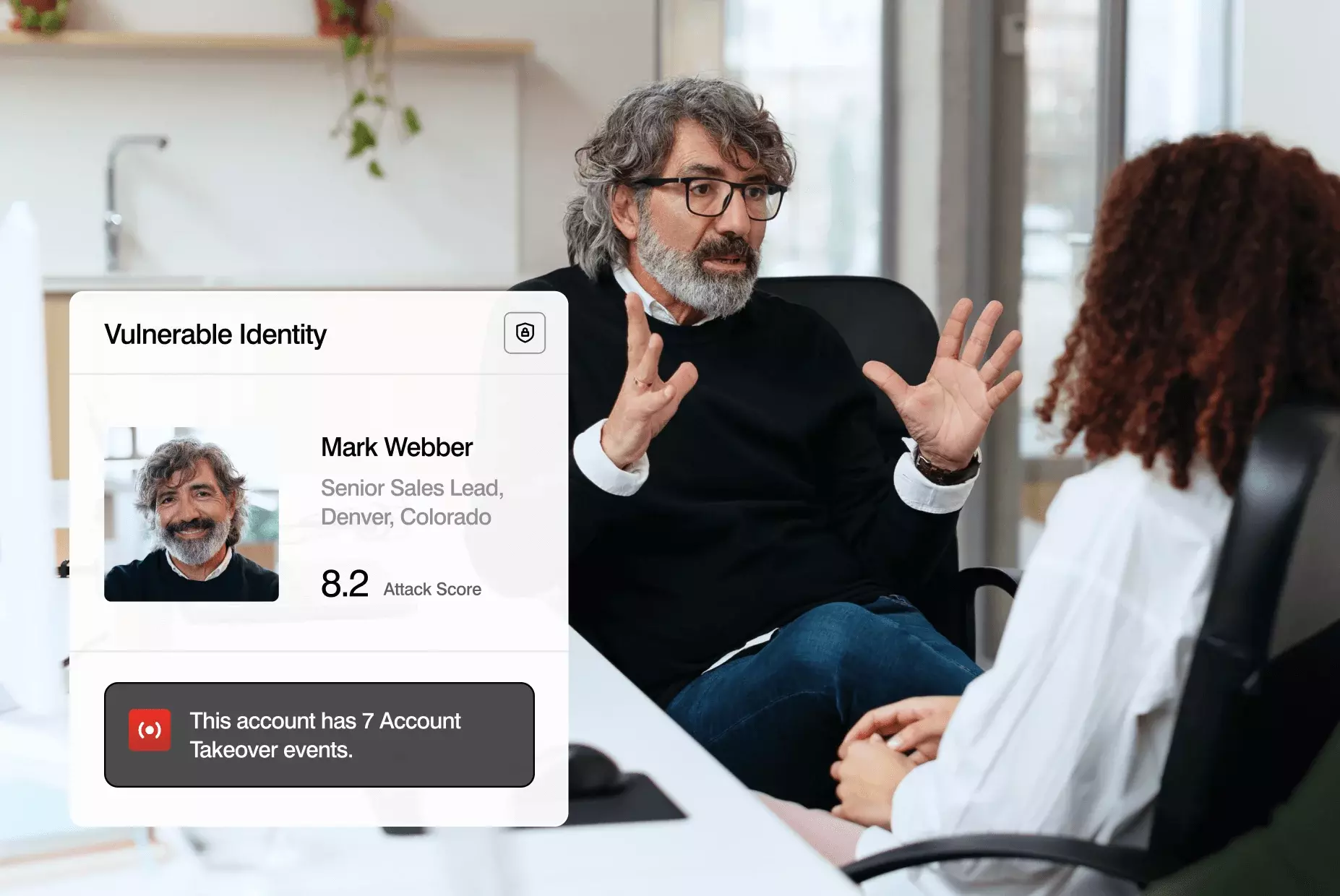
Detect and resolve compromised accounts in minutes, not days
Leverage multiple analytical techniques, machine learning and threat intelligence to quickly detect and resolve compromised accounts. When every second counts, you’ll get alerts and forensic information you can trust. As well as response automation with a click of button.

Stop lateral movement
Remediate available attack paths, remove cached credentials and ensnare attackers in a web of deceptive files and resources that alert you to their presence. Instantly see how attackers got in—and what they have been doing, automatically. Identity Protection remains undefeated in more than 160 red-team exercises (and counting).
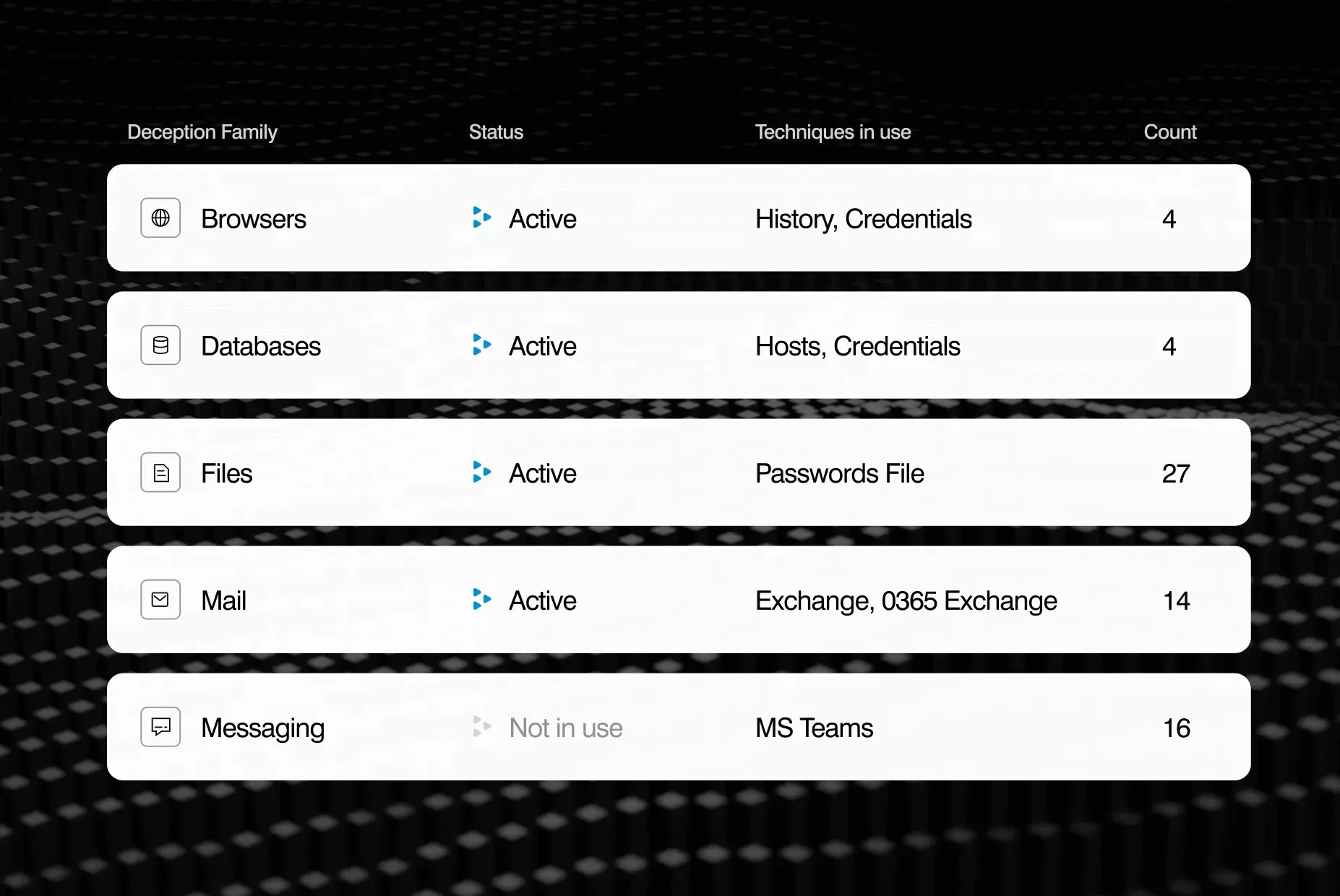
Key features of our Identity Protection product:
Identity security that works across your identity infrastructure
You'll get the industry’s broadest set of integrations and vulnerability analysis for improved defense against identity-centric attacks. Discover and remediate vulnerable identities and active threats in:
- Active Directory
- Entra ID
- Okta
- Office 365
- Google Workspace
- AWS Identity Center
- CyberArk
- Delinea
- Windows, Macs and Linux endpoints
- More than 75 agentless deception techniques

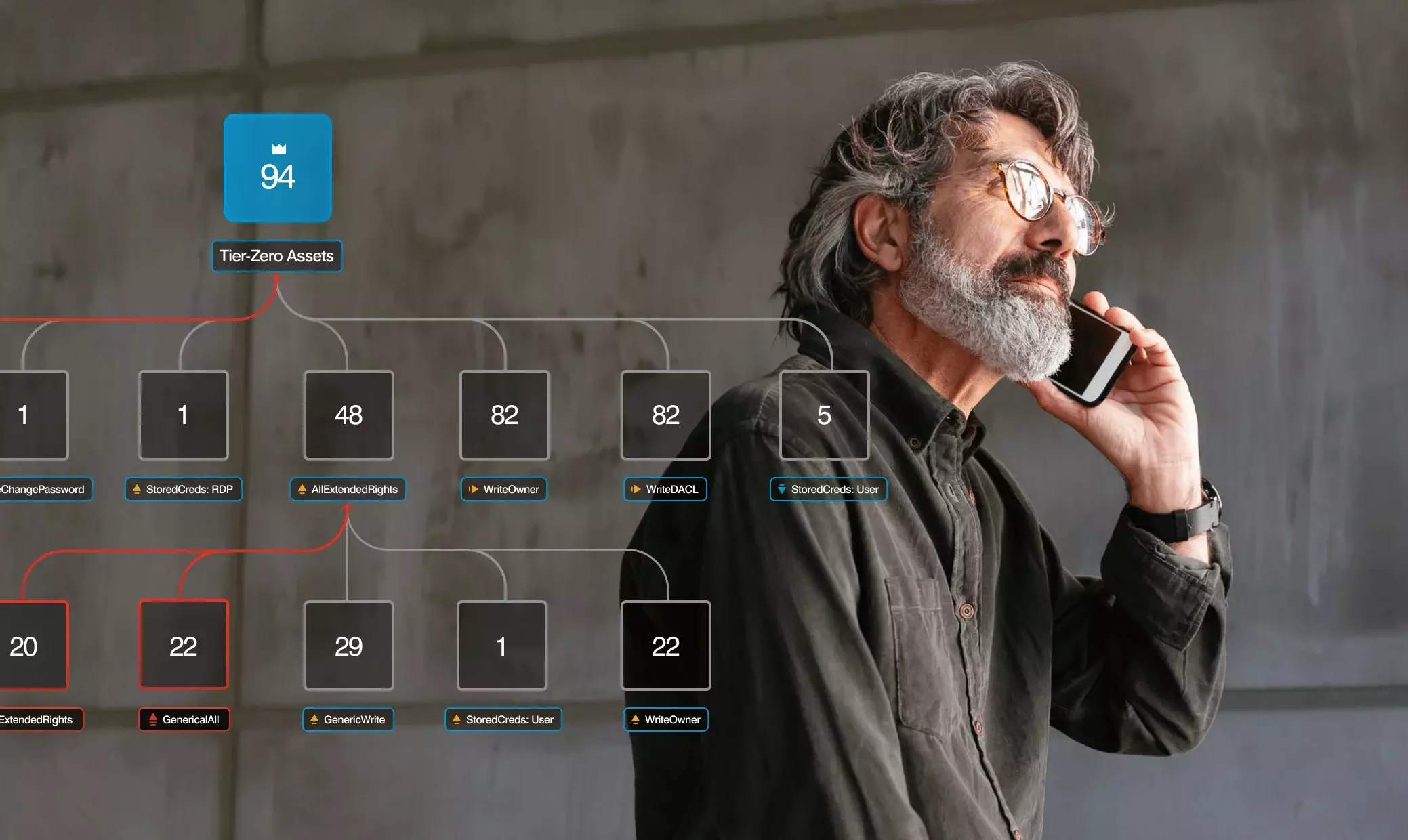
A complete overview of vulnerabilities
Identity Protection creates a complex maze of false paths and tripwires that ensnares attackers as they try to laterally move from host to host toward your organization’s IT crown jewels. It creates fake but authentic-looking:
- Cached credentials
- Browser histories
- Cookies
- Emails
- Microsoft Teams messages
- Office files
- RDP/FTP sessions
- Database credentials
- And more
And best of all, it’s done without agents. So, attackers can’t detect it—let alone bypass it.
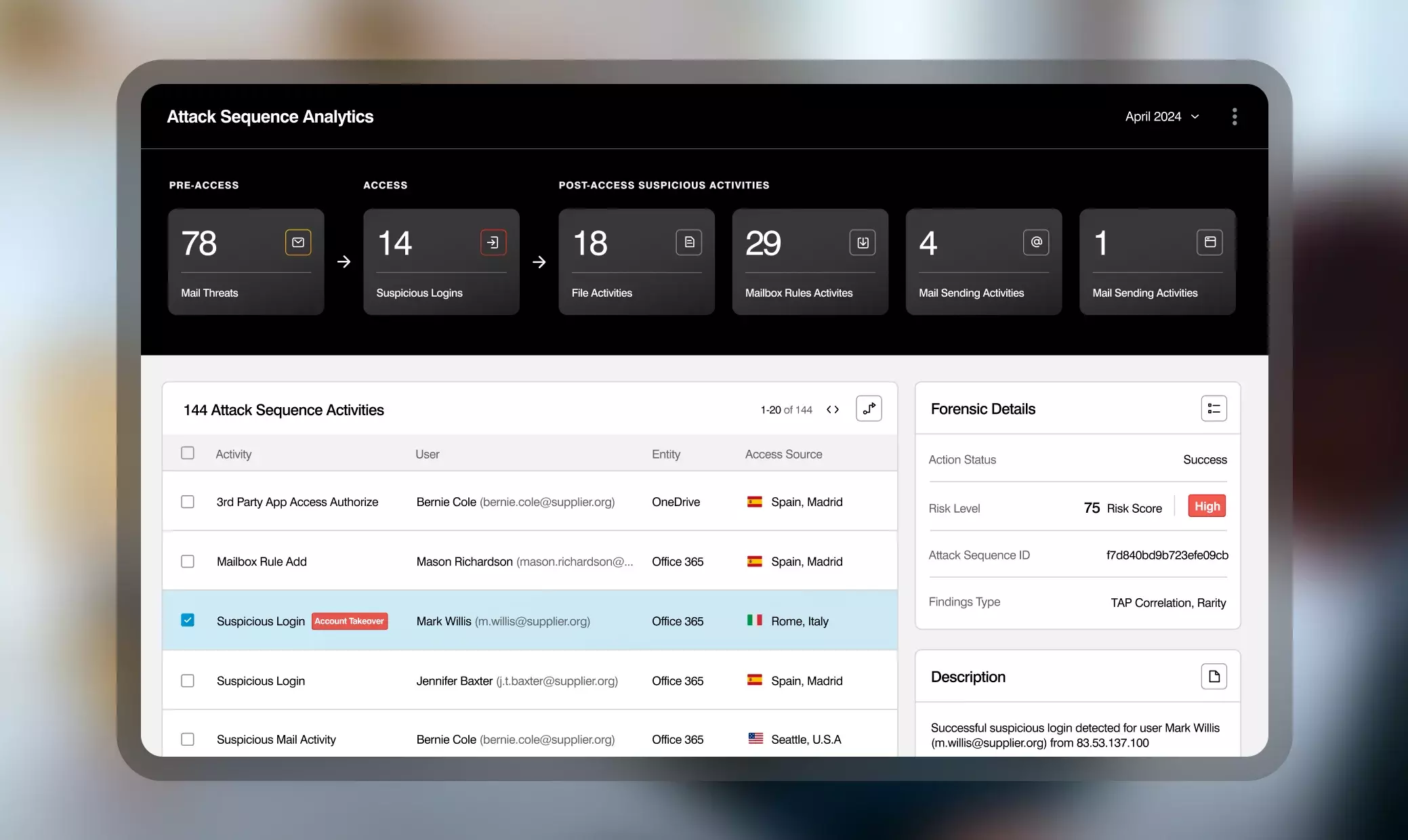
Automated remediation
Get real-time alerts on attackers’ moves and reverse any harmful changes with just a click. Identity Protection streamlines incident response by:
- Suspending compromised accounts
- Reversing attacker-created mailbox rules
- Resetting access to third party cloud apps
- Resetting MFA settings
- Pulling detailed forensic data
- Initiating host quarantines

“The solution is compelling because the console shows your network the way an attacker sees it.” — IT Director, Professional Sports Team
The latest developments in Identity Protection

Solution Brief: Identity Protection
Read More
Identity Threat Detection & Response: Challenges & Solutions

Mitigating Identity Risks, Lateral Movement and Privilege Escalation
Turn people into your best defense
Get Started